By Jamie Ridenhour
Earlier in the year, we discussed the benefits of utilizing an Enterprise Security Risk Management (ESRM) model in An Introduction to ESRM. In short, ESRM provides a more holistic approach to understanding and implementing the varying levels of security needed across the enterprise. In this article, we’ll spend a little more time discussing identifying and analyzing risk, some of the first steps in implementing the ESRM framework.
The process of implementing ESRM begins with developing a comprehensive understanding of what an organization’s most important assets are and then identifying and prioritizing the risks to those assets. As we mentioned in the earlier article, the strength of ESRM lies in the concept of business leaders taking responsibility for their assets and working closely with the security team to manage the associated risks.
The assets that need to be considered go well beyond the typical physical assets that are shown on a balance sheet. Certainly equipment, vehicles, infrastructure, and other tangible items need to be considered, but intangible assets must be a part of the calculation as well. Intellectual property, goodwill, and brand perception are all examples of intangible assets. In addition, the people that make up an organization are an important business asset that must be accounted for. Having asset owners throughout the organization involved in the process ensures that the list of assets is as complete as possible.
Once the list of assets has been developed, a value needs to be assigned. This concept can be a little daunting. Some assets may have both physical and intangible value to a business. At first glance, it seems easy to assign a value to a computer file server – just look up the replacement cost. But quantifying risk is particularly difficult when it comes to cybersecurity. What about the data that resides on the server? Will the business feel a negative impact if that data is lost or compromised? Will productivity be affected? It’s obviously much harder to assign a dollar value to these intangible items. For this reason, valuation is more about prioritizing assets than assigning a price tag. Understanding which assets are most important to the organization is the goal of this exercise.
This is why the expertise of asset owners is so important. Who is better to analyze the potential impact of damage to or loss of an asset than the person who manages it and knows the business functions that rely on it? They are the people in the organization who fully understand the real value of the asset.
The next step is to evaluate the risk to each asset. Brainstorming, checklists, and simulations are all effective ways of identifying risks. It is useful to think pessimistically when trying to identify risks. “What’s the worst that could happen?” is not a bad place to start.
When assessing risk, a broad range of threats should be considered, including natural threats (hurricanes, tornadoes, floods, and earthquakes), cyber threats (data leakage, ransomware, DDOS attacks, etc.), physical criminal threats (theft, violence against staff), terrorists (active shooter, explosive device), and accidents.
An examination of vulnerabilities is also a good way to identify risks. By looking for weaknesses in assets or ineffective controls, vulnerabilities can often be identified, and vulnerabilities can lead to risks. A poorly lit and unguarded entrance may lead to an increased risk of theft, for instance. This is an area where the partnership with the security team comes into play since protection experts have the experience to identify vulnerabilities.
When assets and risks have been identified, it is now time to analyze and evaluate. Once again, the goal is to arrive at an understanding of the relative severity of each risk rather than a precise monetary cost.
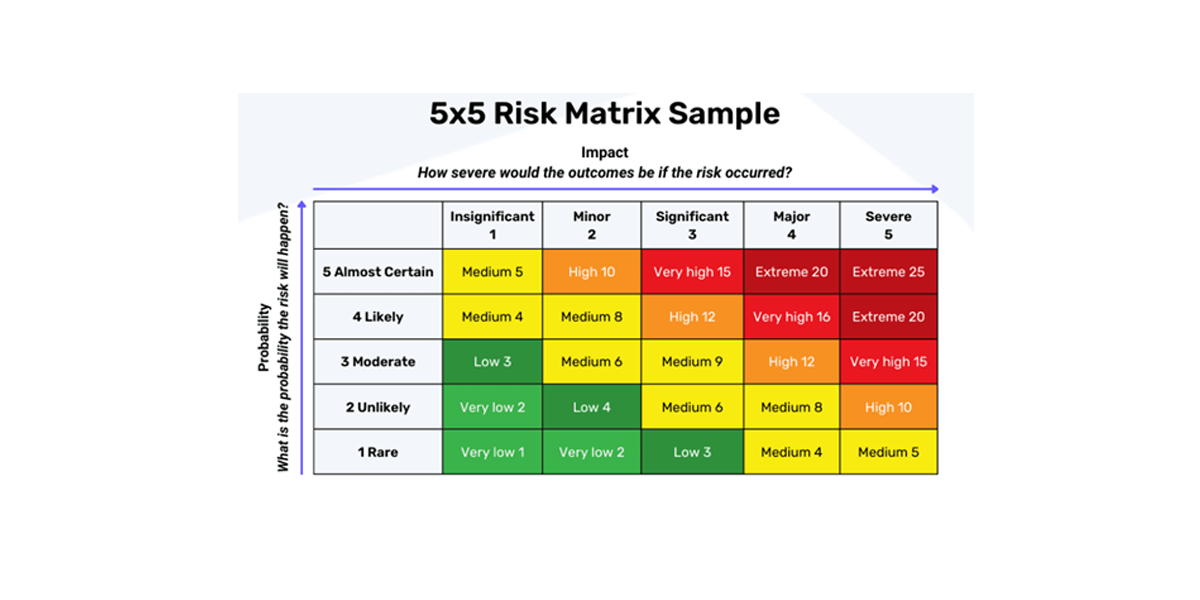
Analyzing risk involves estimating the likelihood that the risk will occur and the relative impact to the organization if it does. For example, common theft may have a high probability of occurring, but a relatively low cost to a store whereas theft of customer information in a data breach may have a lower probability, but a potentially high impact. Analysis results can be expressed qualitatively (low, medium, high) or quantitatively (estimated financial impact, percentage probability, time lost, etc.).
The best way to prioritize risks is to use a risk matrix such as the one shown at the beginning of this article. This type of matrix allows an organization to visualize which risks should get the most attention. From there, the discussion should focus on how to respond to each risk. Typical strategies include avoiding, reducing, transferring, or accepting. Both asset owners and security professionals are likely to have useful input on risk treatments.
One of the most important aspects of the ESRM framework is that it should be treated as a continuing process. The information gathered through identifying and analyzing risk should be fully documented and made available to all stakeholders. The risk list should be reviewed at least annually, and the full analysis repeated every few years. Doing so helps make sure evolving risks are identified and at the same time provides an opportunity to keep stakeholders involved in the ESRM process.