By Jamie Ridenhour
ESRM is a widely discussed topic in the security field. The concept of Enterprise Security Risk Management (ESRM) became mainstream when it was adopted by the ASIS International Board of Directors in 2016. While it may encompass ideas that an organization and its security professionals have already implemented, it provides for a more holistic approach to understanding and implementing the varying levels of security needed across the enterprise.
ASIS International describes ESRM as, “a strategic approach to security management that ties an organization’s security practice to its overall strategy using globally established and accepted risk management principles.” In plain terms, the practice of ESRM seeks to create a better and more transparent relationship between an organization’s management, the organization’s stakeholders, the organization’s mission, and the security professionals whose role it is to protect those assets both tangible and intangible.
ESRM addresses mitigating risk from physical security, cybersecurity, information security, personal security loss prevention, organizational resilience, brand protection, travel risk, supply chain security, business continuity, crisis management, threat management, fraud risk management, and workplace violence prevention. It should be evident that this list encompasses much more than we typically consider to be part of the normative professional security domain.
This strategic approach requires a shift in the security paradigm away from the typical siloed treatment of security as a separate entity that is tolerated but not necessarily a part of the decision making process. In the ESRM framework, business leaders, managers, and supervisors become owners of the risks and therefore have more incentive to work with the security team to make sure assets are properly protected. The value of this approach is that risks are more efficiently prioritized by those with the best understanding of the organization’s mission and strategic goals.
The weight of ESRM implementation does not fall entirely on business leaders, though. The security team also must play an important part by developing a better understanding of the most important assets and how best to protect them. Rather than the more typical task based approach to security, the team now becomes a partner in advancing the overall mission. This risk-based approach incorporates the idea that a security team cannot effectively protect what they do not understand. A universal understanding of the organization’s needs, priorities, and mission are a critical part of the ESRM process.
The result is that business stakeholders are more engaged with security professionals and can develop a more consistent and accurate understanding of the role of security while security also becomes more knowledgeable and in step with the operational side of an organization. It also helps management to better identify, prioritize, and efficiently manage risks. Security professionals gain a more effective relationship for evaluating and elevating security risks to management. Transparency and communication are important benefits of ESRM implementation.
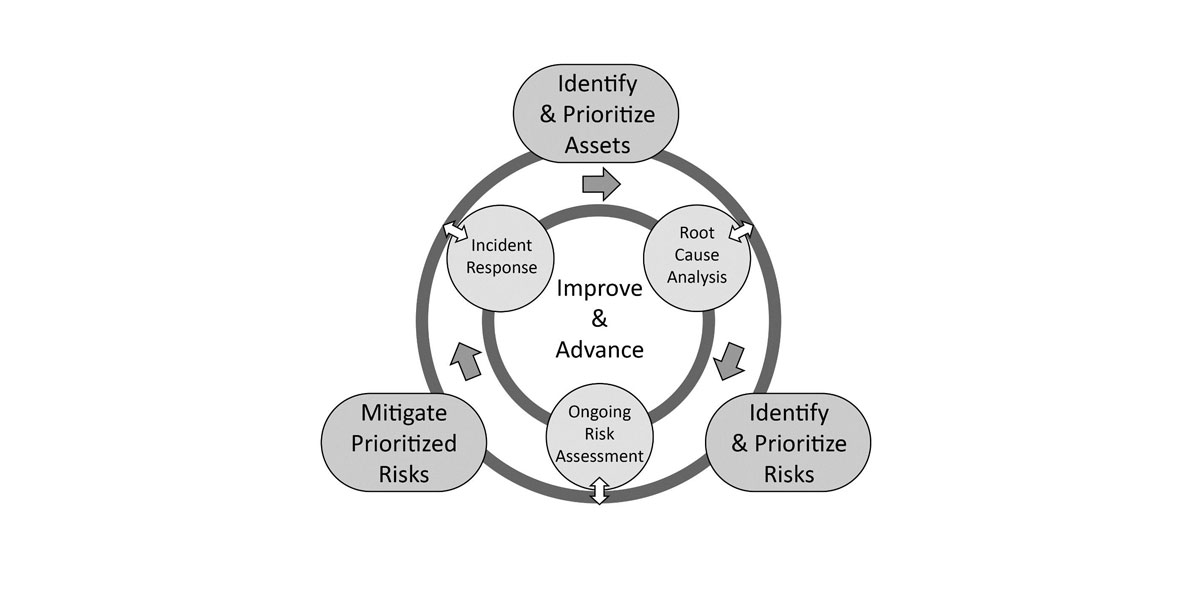
The ESRM cycle includes four processes:
- Identifying and prioritizing assets – Assets are defined as anything that adds value to the organization and asset owners are responsible for mitigating risk to an acceptable level. Assets are prioritized based on the organization’s goals and objectives. Value can be based on cost or operational and reputational impact of loss.
- Identifying and prioritizing risk – Risk assessments are made using the enterprise risk assessment methodology which helps determine risk level based on threats, vulnerabilities, impact, probability, and asset value. The risk level is then compared to a risk acceptable value to determine the risk priority.
- Mitigating Risk – After risks are prioritized, those that are categorized as unacceptable must be brought to an acceptable level through mitigation. Mitigation may involve physical security, electronic controls, video surveillance, security awareness training, and digital security among others.
- Continuous improvement – This is perhaps the most compelling idea in the ESRM cycle since it makes the cycle an iterative approach to continually improving the process. Investigations, analysis, information sharing, and incident response all contribute to continuous improvement.
Stakeholders and security professionals working together to identify, prioritize, and mitigate risks and then continuously evaluate the process ensures that risks are understood and dealt with as effectively as possible. Any activity that security performs will be in response to an identified risk, which is in turn tied to a critical asset. The value is achieved through ensuring that the organization does not experience harm to or loss of assets.
Another benefit of the ESRM process is that the focus on educating stakeholders about the risks and mitigation strategies for the assets they own creates an environment where security is part of the identity of the organization. By continually repeating the ESRM cycle, enterprise security functions can be analyzed and refined like any other business process.
There are also significant benefits for the security team. ESRM gives the team the ability to have a better relationship with business units and to become more well-rounded as a result. Developing a deeper understanding of the organization’s mission and strategy is rewarding in itself, but also empowers enterprise security to have better conversations with stakeholders. It facilitates a shift from just being “those folks in security” to sending the message that security is here to help the organization meet its goals.
ESRM can be beneficial to stakeholders, security professionals, and the organization as a whole. If it sounds like a good fit for your organization, we highly recommend checking out the ASIS International ESRM documentation. We’ll dive into ESRM implementation in a later article, but an improved understanding of the organization’s strategy, identifying stakeholders and defining the role of security are high level starting points.